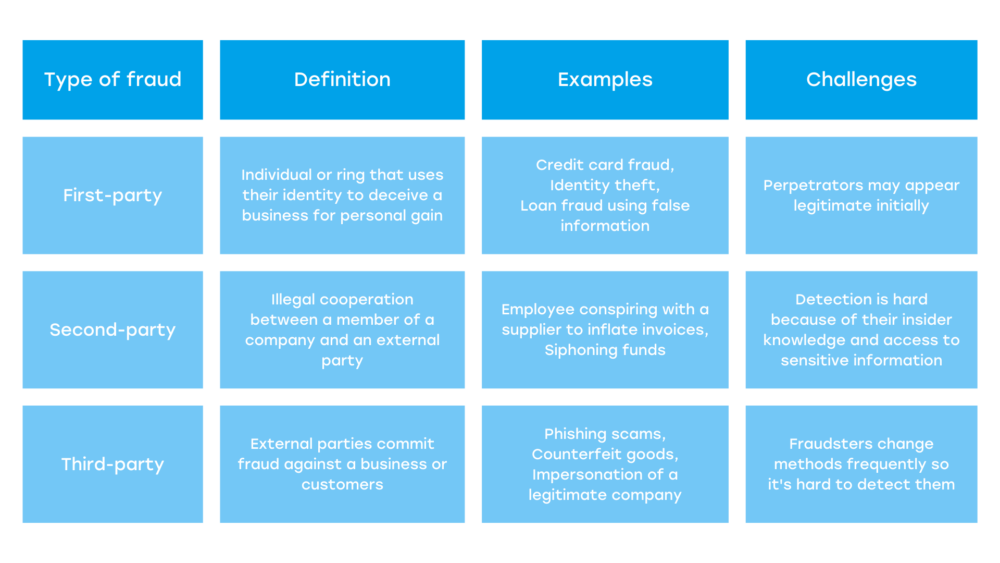
As technology advances, so do fraudulent activities, along with their complexity. Merchants are facing new challenges each day because criminals gain new ways to exploit vulnerabilities. Among these fraudulent activities, it’s good to know what second-party fraud is, its differences as opposed to first-party and third-party frauds, and how to avoid and prevent them.
This type of fraudulent activity is also on the rise, and in 2022, consumers reported staggering losses of nearly $8.8 billion to fraud. According to Federal Trade Commission data, it’s a significant increase of 30% from the previous year. The impact on merchants is large, as every dollar lost translates to $3.75 total. This only goes to show just how important it is to put safety measures in place and prevent this type of fraud from happening.
What Is Second-Party Fraud Exactly?
A second-party external fraud happens when an individual shares their personal data or credentials with someone who uses them for fraudulent activities. The data may involve their identity, bank account details, or contact information. The usual purpose of this is for unlawful financial gain, money laundering, and taking loans illegally.
This shared personal data can also be used to create a synthetic identity. The victims can be completely unaware that their information was stolen, or fraudsters target the elderly, young, or other vulnerable victims.
This type of fraud can hit merchants hard. When it happens, it can lead to losing revenue and incurring fees, all because they face the burden of chargebacks. No matter how good their customer service is, their reputation also takes a hit as customers lose trust and leave negative reviews, leading to decreased sales.
Types Of Identity Theft
According to Investopedia, thieves can gain personal data in many ways. The most obvious ways include sifting through trash cans to find bank statements and credit card information or using computer technology to obtain credit card and other information. There are several types of identity theft, including the following:
- Financial identity theft happens when someone uses another person’s identity to obtain credit, goods, services, or benefits. It is the most common type of identity theft.
- Social Security identity theft happens when fraudsters use someone else’s Social Security number to apply for credit cards and loans or to receive benefits such as medical or disability support without paying outstanding balances.
- Medical identity theft happens when a fraudster poses as another person to access medical care without bearing the cost.
- Synthetic identity theft happens when a mix of real (often stolen) and fake information is used to create a new identity, open fraudulent accounts and make unauthorized purchases.
- Child identity theft happens when a child’s identity is used for various personal gains, such as obtaining housing, employment, or loans. Fraudsters are often family members or close acquaintances.
- Tax identity theft happens when a fraudster uses someone else’s personal information, including Social Security numbers, to file a false tax return and steal a refund.
- Criminal identity theft happens when a criminal impersonates another individual during an arrest to avoid legal consequences, such as serving a summons or revealing an existing warrant.
Once fraudsters get their hands on someone’s personal information, they can damage their credit score and other personal information.

Second-Party Fraud Examples
When a merchant ventures into e-commerce waters, their tasks are not only to choose merchant services and credit card processing and then set up a merchant account. They should also be on the lookout for any fraudulent activity unless they want to suffer substantial losses. Being vigilant means understanding how different kinds of second-party fraud work.
Money Muling (Money Laundering)
Money laundering (muling) happens when a fraudster uses PII (personally identifiable information) to open a bank account. They use it to receive and transfer stolen funds. Both the mule (the person providing details) and the scammer are responsible, even if the mule is unaware.
Chargeback Fraud
Chargeback scams involve credit card information given to scammers when they shop using a tablet, computer, or phone not linked to the actual cardholder. The thief keeps the goods, while the cardholder reports the purchases as fake and gets their money back from the bank. This affects both the issuing bank and the merchant.
Fake Merchant Fraud
Fake merchant fraud happens when a fraudster pretends to be the e-commerce store and has the customer buy fake goods from them. The cardholder asks their bank for a refund when they don’t receive the things, which makes sense since they don’t exist. In the end, the fraudster divides the profit while the bank takes a financial hit.
Second-Party Loan Fraud
Second-party loan fraud is a type of scam that targets financial institutions. The fraudster applies for a loan, usually a mortgage, using the victim’s personally identifiable information. The borrower is unable to repay the loan, and the property then needs to be foreclosed. That’s when the fraudster contacts the lender and offers to decrease their losses by buying the property at a reduced price.
Gift Card Fraud or Laundering
Gift card fraud or laundering should be very well-known among small businesses that offer gift cards. This type of fraud involves personal bank account information that ends up in a scammer’s hands. The scammer then puts money into the person’s account and buys gift cards online with it. When these are sent to the scammer, they are basically used to turn money that was obtained illegally into real gift cards.
Leading the Witness
Second-party fraud can have legitimate origins. They happen sometimes when financial institutions launch disputes on behalf of clients, and a transaction that is flagged as a possible scam may generate a chargeback. A consumer’s bank sends a post-purchase text to confirm an earlier charge.
The consumer could easily judge the transaction as invalid and suspicious. The bank undertakes a chargeback on the cardholder’s behalf, despite the lawful purchase. Even if the charge has been settled when the consumer provides feedback, the financial institution must open an inquiry to review the claim.
How Does It Affect Businesses
Second-party fraud poses a huge risk to businesses because it can lead to substantial losses. Chargebacks, for example, are designed to protect customers from fraud but can prove to be time-consuming and costly for merchants. Another issue is that it can be hard to find and reveal this type of fraud. A merchant may think that a customer requesting a chargeback is involved in a scam, but to prove it, they must show proof that the customer is connected to the scammer.
Keep in mind that every unanswered customer dispute, whether valid or invalid, makes the merchant appear negligent. This makes it easier to blame the merchant, even if the fraud isn’t their fault. It’s especially true for chargebacks that originate as second-party fraud, where it’s nearly impossible to trace the crime back to the perpetrator. As a result, both banks and merchants are left with the burden of refunding the customer.

What Can a Merchant Do
As a merchant, the best way to combat second-party fraud is to develop a long-term strategy. While it may seem challenging to detect or prove all instances of scams, there are several steps you can take to protect your business. A great start for e-commerce fraud prevention would be to start blacklisting suspicious users or accounts to prevent repeat attacks. A merchant wary of e-commerce fraud should watch out for the following behaviors:
- High-ticket value purchases,
- A high volume of transactions in a short period,
- An unusually high number of returns,
- Purchases that do not match previous buying patterns.
Additionally, merchants should choose merchant services from experienced credit card processing companies that offer a multilayer solution for fraud detection.
Additional Ways to Prevent This Type of Fraud
When protecting your business from fraud, it’s also very important to check customer information to make sure it is correct. You should check addresses, phone numbers, and information that doesn’t seem legitimate. It’s also crucial to teach workers how to spot signs of fraud and how important it is to follow strict verification and monitoring procedures.
Another important part of fraud prevention is to improve overall protection. This means using advanced security measures such as two-factor authentication, encryption, and secure payment gateways to protect sensitive information. It’s also crucial to be PCI compliant, as it sets the standard for securing credit card information and helps in reducing vulnerabilities.
In the end, it’s essential to respond quickly to customer complaints. Dealing with disputes in a timely manner can prevent your business from being flagged as negligent. On top of that, you should also stay on top of the latest fraud trends and strive to update protection strategies.

Stay Ahead of Fraudsters With Merchant Chimp
Second-party fraud is not to be taken lightly, as it can cause big problems for businesses, and cost them money. However, there are ways for merchants who use credit card processing services to protect themselves. From PCI compliance to other security measures, your business can stay ahead of the latest trends among fraudsters.
But don’t worry – a professional credit card processing company such as Merchant Chimp can guard your transactions. We offer fraud prevention solutions with our processing services, and we can help your business stay secure. Contact us and find everything you need – from discount programs to expert guidance on various payment options.